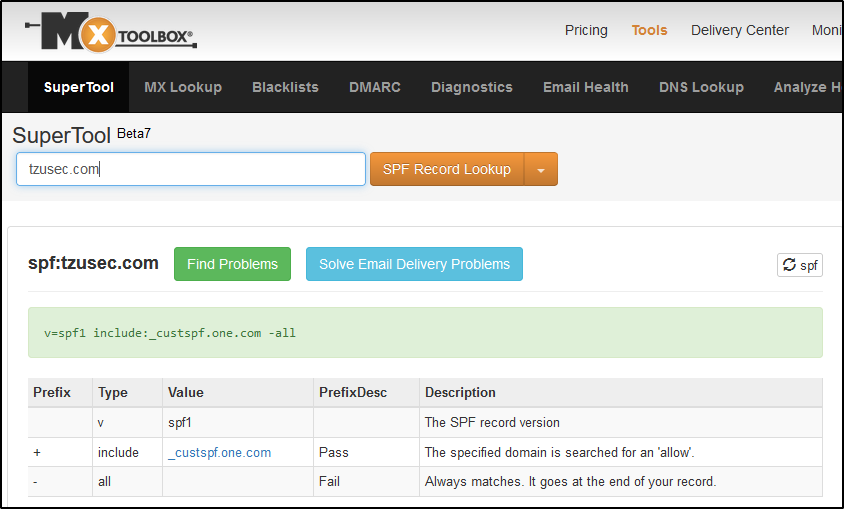
This guide will show you how you can launch cmd and Powershell with help from Microsoft Paint. Sometimes organisations environments are being locked down and are preventing users from right clicking and opening tools such as cmd.exe or powershell.exe. When I face that during a penetration test I usually try this simple mspaint hack to check if I can get around the organisations defensive measures.
How to launch Command Prompt (cmd.exe)
- Open Paint
- Press Resize
- Configure the size
- Uncheck “Maintain Aspect Ratio”
- Click on “Pixels”
- Horizontal: 6
- Vertical: 1
- Press OK
- Zoom in so you can see the pixels.
- The next step is to color these six pixels in the correct colors. Press “Edit colors’ and then change the colors for each pixel according to the list below. You modify the colors by changing the values of Red, Green and Blue:
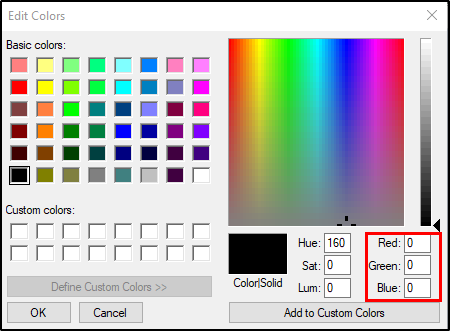
Colors for each pixel:- Red(10), Green(0), Blue(0)
- Red(13), Green(10), Blue(13)
- Red(100), Green(109), Blue(99)
- Red(120), Green(101), Blue(46)
- Red(0), Green(0), Blue(101)
- Red(0), Green(0), Blue(0)
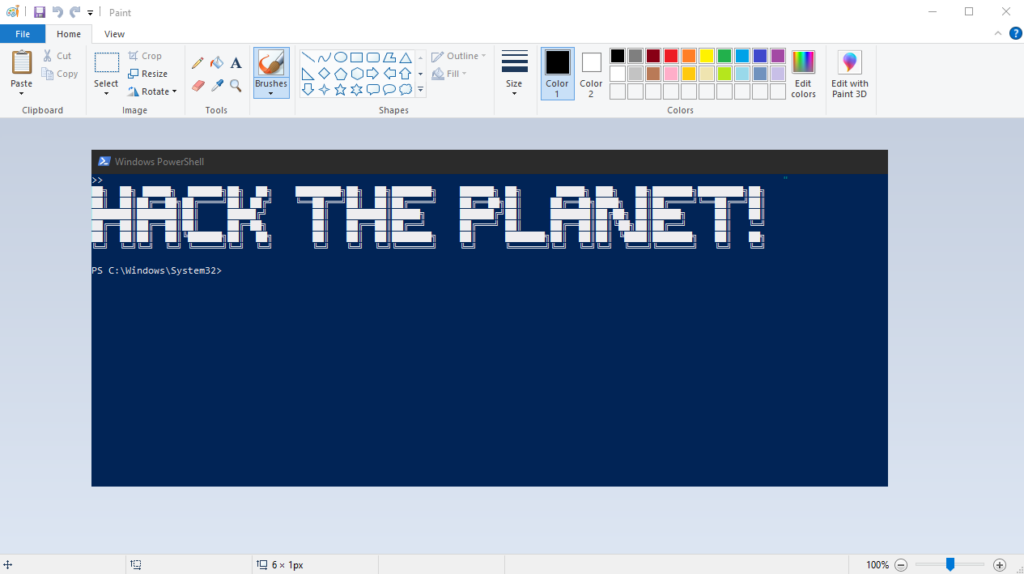
- When you have filled the pixels with the correct colors it should look like this:
- The next step is to save the file by pressing “Save As” and then changing file format to “24-bit Bitmap”.
- Now the last step is to change the file format of the file from .BMP to .BAT
- Now just double click on the new .BAT-file.
- Voila
How to launch Powershell
The process is the same for powershell, the only difference are the colors. Instead of the colors above use these:
- Red(10), Green(0), Blue(0)
- Red(13), Green(10), Blue(13)
- Red(119), Green(111), Blue(112)
- Red(115), Green(114), Blue(101)
- Red(108), Green(101), Blue(104)
- Red(0), Green(0), Blue(108)
How it works:
What we do is changing the color of the six pixels so that they in heaxdecimal represents ‘cmd.exe’/’powershell’. When we save the file to .BMP the encoding algorithm converts the RGB colors to ASCII data. When that is done and we change the file format to .BAT the .BAT script containts the instruction ‘cmd.exe’/’powershell’ that will be executed when we double click on the script.
I hope you did found this useful. It’s a pretty cool trick to have in your arsenal during penetration tests.
// Rickard Carlsson